Yale College will introduce a Certificate in Quantum Science and Engineering in Fall 2025, addressing the national and global shortage of talent in the field. The program, managed by the Yale Quantum Institute, will offer undergraduates a structured pathway into quantum science and engineering, requiring five course credits, including one core course and four electives. The certificate is designed to be accessible to students from various backgrounds and departments, including Applied Physics, Computer Science, and Chemistry. No prior knowledge of quantum mechanics is required, and the program aims to attract individuals from different backgrounds and skills to contribute to the future of quantum systems. Student interest has been significant, with a recent survey showing an overwhelming number of respondents interested in pursuing the certificate. The career opportunities for graduates with quantum expertise are expanding rapidly across multiple sectors, including tech companies, pharmaceutical research, financial services, and logistics. The creation of the certificate program aligns with Yale's broader efforts in quantum education and the recommendations of the University Science Strategy Committee.
Read full article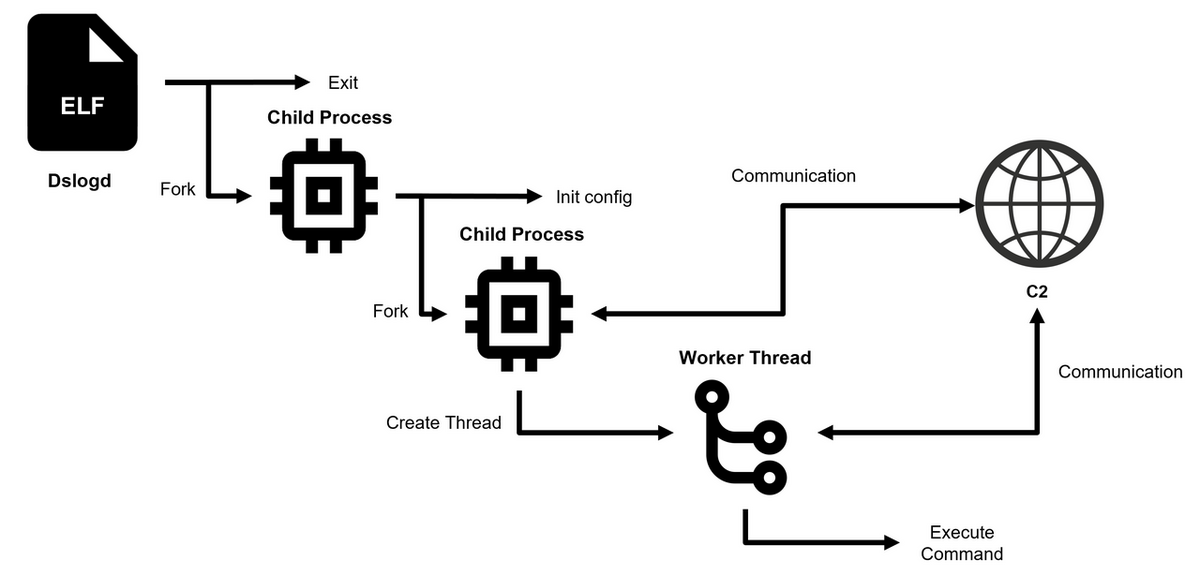
April 25, 2025 • By Pierluigi Paganini
Here is a concise summary of the news article, within the 8173 token limit: Multiple cybersecurity incidents have been reported, including data breaches at MTN Group, DaVita, and Yale New Haven Health, affecting millions of patients. Ransomware attacks have targeted various organizations, such as Interlock, which leaked data from a kidney dialysis firm, and LockBit, which exploited Fortinet Firewall flaws. Several vulnerabilities have been discovered, including a zero-day in Ivanti Connect Secure, a critical flaw in Apache Parquet's Java Library, and a flaw in Verizon's iOS Call Filter app. Nation-state actors, such as China-linked APT groups, have been involved in various cyberattacks, including the exploitation of a recently disclosed OttoKit WordPress plugin flaw and the use of a custom malware called JumbledPath to spy on U.S. telecom providers. Other notable incidents include a cyberattack on the Micronesian state of Yap, a ransomware attack on the New York Blood Center, and a data breach at the Italian data protection authority Garante. U.S. CISA has added several flaws to its Known Exploited Vulnerabilities catalog, including Apple products, Microsoft Windows, and Cisco Small Business RV Series Routers. Overall, the cybersecurity landscape remains complex, with various threats and vulnerabilities emerging regularly.

April 25, 2025 • By Robin
Dority & Manning, a US patent law firm, is hiring. They offer a dynamic environment where individuals can grow and succeed. The firm represents diverse organizations in intellectual property law, including start-ups and Fortune 100 corporations, and works with clients in innovative technologies like AI and quantum computing. To apply, email a resume to recruiting@dority-manning.com. The job location is Greenville, SC, or Raleigh, NC.
April 25, 2025 • By jpugachevsky@businessinsider.com (Julia Pugachevsky)
Mike Crabtree, Director of Data Engineering at Ford, shares his story of overcoming a crowded job market after the 2008 recession. With an associate's degree in industrial mechanics and electronics engineering, he struggled to stand out. To differentiate himself, he took paid online courses from platforms like Coursera, edX, and Udacity, earning certifications in business analytics, leadership skills, and more. This helped him pivot into data science and eventually land a job at Ford as a data scientist. To "recession-proof" a job, Crabtree suggests three strategies: 1. Identify and address skill gaps by taking challenging online courses to improve technical and soft skills. 2. Develop critical thinking skills by learning to assess direction, build business acumen, and make confident decisions. 3. Form strong workplace relationships by being assertive, improving communication and confidence through public speaking courses, and sharing suggestions in a clear and approachable way. By following these strategies, individuals can increase their chances of success and stability in their careers, even in a tough job market.
April 25, 2025 • By ReversingLabs US, Inc.
ReversingLabs has launched support for eXtended Bill of Materials (xBOM) capabilities with Spectra Assure, providing software producers and enterprise buyers with visibility into components, services, and risks within complex software ecosystems. The new features include Cryptographic Bill of Materials (CBOM), Software-as-a-Service Bill of Materials (SaaSBOM), and Machine Learning Bill of Materials (ML-BOM). This innovation offers unprecedented transparency and empowers organizations to drive targeted risk reduction efforts. The xBOM capabilities enable businesses to go beyond traditional SBOMs, addressing emerging risks such as quantum computing threats, interconnected cloud services, and AI-driven vulnerabilities. With Spectra Assure, enterprise buyers can source information without relying on vendors, eliminating the need for security questionnaires and incomplete visibility. The new xBOM support helps software producers and buyers adhere to strict compliance mandates and enables regulatory compliance. ReversingLabs is leading the charge in redefining software transparency with its xBOM capabilities, empowering customers to build and buy software with confidence.

April 25, 2025 • By Pierluigi Paganini
Here is a concise summary of the news article in 8173 tokens or less: Multiple cybersecurity incidents have been reported recently. MTN Group disclosed a data breach, and the CEO of a cybersecurity firm was charged with installing malware on hospital systems. JPCERT warned of DslogdRAT malware, and SAP NetWeaver had a zero-day exploit allegedly used by an initial access broker. Operation SyncHole targeted supply chains in South Korea, and Interlock ransomware gang leaked data from a kidney dialysis firm. Yale New Haven Health had a data breach impacting 5.5 million patients. Crooks exploited the death of Pope Francis on WhatsApp, and Android spyware was hidden in mapping software targeting Russian soldiers. A crypto mining campaign targeted Docker environments, and the xrpl.js Ripple cryptocurrency library was compromised in a supply chain attack. British retailer Marks & Spencer managed a cyber incident, and Chinese cybercriminals released a tool for payment fraud. Millions of SK Telecom customers were at risk due to a USIM data compromise. Japan's FSA warned of unauthorized trades via stolen credentials, and Kimsuky APT exploited a BlueKeep RDP flaw. Russia-linked APT29 targeted European diplomatic entities with malware. Security Affairs reported on various malware news, including attacks on hospitals, telecom providers, and cryptocurrency platforms. U.S. CISA added several flaws to its Known Exploited Vulnerabilities catalog, including Apple products, Microsoft Windows, and Linux Kernel flaws. Multiple companies, including Legends International, Conduent, and Hertz, disclosed data breaches. New malware variants, such as ResolverRAT and SuperCard X, were discovered, and Tycoon2FA phishing kits were updated. China admitted to its role in Volt Typhoon cyberattacks, and Symbolic Link trick allowed attackers to bypass FortiGate patches. Laboratory Services Cooperative had a data breach impacting 1.6 million people, and Palo Alto warned of brute-force login attempts. Gamaredon targeted the military mission of a Western country in Ukraine. U.S. CISA added Linux Kernel and VMware ESXi flaws to its catalog, and VMware fixed three actively exploited zero-days. Digital nomads were warned of the risk of infiltrated employees, and Google fixed two actively exploited Android flaws. CISA maintained its stance on Russian cyber threats despite policy shifts. A ransomware attack hit the Micronesian state of Yap, and LockBit ransomware developers were extradited. Medusa ransomware targeted critical infrastructure organizations, and China-linked APT UNC3886 targeted EoL Juniper routers. U.S. CISA added Microsoft Windows flaws to its catalog, and Microsoft fixed six actively exploited zero-days. A cyberattack hit Ukraine's national railway operator, and Chinese APT Weaver Ant infiltrated a telco in Asia. The popular xrpl.js Ripple cryptocurrency library was compromised, and British retailer Marks & Spencer managed a cyber incident. Multiple companies, including DaVita and Yale New Haven Health, disclosed data breaches. New malware variants, such as Ballista Botnet and Astral Foods, were discovered, and Cloak ransomware group hacked the Virginia Attorney General's Office. U.S. CISA added Ivanti Connect Secure and Policy Secure flaws to its catalog, and a member of the Scattered Spider cybercrime group pleaded guilty. China-linked group UNC5221 exploited Ivanti Connect Secure zero-day, and Europol-led operation shut down a CSAM platform. New Triada Trojan came preinstalled on Android devices, and FIN7's Anubis backdoor allowed full system control on Windows. U.S. CISA added Apache Tomcat flaw to its catalog, and Apple backported fixes for three actively exploited flaws. A spike in Palo Alto Networks scanner activity suggested imminent cyber threats, and Microsoft warned of a critical flaw in Canon printer drivers. France's antitrust authority fined Apple €150M for issues related to its App Tracking Transparency. Malicious NPM packages targeted PayPal users, and Tycoon2FA phishing kits were updated. Russia-linked Gamaredon targeted Ukraine with Remcos RAT, and CoffeeLoader used a GPU-based packer to evade detection. Morphing Meerkat phishing kits exploited DNS MX records, and U.S. CISA added Cisco Smart Licensing Utility flaw to its catalog. Denmark warned of increased state-sponsored campaigns targeting European telcos. A ransomware attack hit the Micronesian state of Yap, and LockBit ransomware developers were extradited. Medusa ransomware targeted critical infrastructure organizations, and China-linked APT UNC3886 targeted EoL Juniper routers. U.S. CISA added Microsoft Windows flaws to its catalog, and Microsoft fixed six actively exploited zero-days. A cyberattack hit Ukraine's national railway operator, and Chinese APT Weaver Ant infiltrated a telco in Asia. The popular xrpl.js Ripple cryptocurrency library was compromised, and British retailer Marks & Spencer managed a cyber incident. Multiple companies, including DaVita and Yale New Haven Health, disclosed data breaches. New malware variants, such as Ballista Botnet and Astral Foods, were discovered, and Cloak ransomware group hacked the Virginia Attorney General's Office. U.S. CISA added Ivanti Connect Secure and Policy Secure flaws to its catalog, and a member of the Scattered Spider cybercrime group pleaded guilty. China-linked group UNC5221 exploited Ivanti Connect Secure zero-day, and Europol-led operation shut down a CSAM platform. New Triada Trojan came preinstalled on Android devices, and FIN7's Anubis backdoor allowed full system control on Windows. U.S. CISA added Apache Tomcat flaw to its catalog, and Apple backported fixes for three actively exploited flaws. A spike in Palo Alto Networks scanner activity suggested imminent cyber threats, and Microsoft warned of a critical flaw in Canon printer drivers. France's antitrust authority fined Apple €150M for issues related to its App Tracking Transparency. Malicious NPM packages targeted PayPal users, and Tycoon2FA phishing kits were updated. Russia-linked Gamaredon targeted Ukraine with Remcos RAT, and CoffeeLoader used a GPU-based packer to evade detection. Morphing Meerkat phishing kits exploited DNS MX records, and U.S. CISA added Cisco Smart Licensing Utility flaw to its catalog. Denmark warned of increased state-sponsored campaigns targeting European telcos. A ransomware attack hit the Micronesian state of Yap, and LockBit ransomware developers were extradited. Medusa ransomware targeted critical infrastructure organizations, and China-linked APT UNC3886 targeted EoL Juniper routers. U.S. CISA added Microsoft Windows flaws to its catalog, and Microsoft fixed six actively exploited zero-days. A cyberattack hit Ukraine's national railway operator, and Chinese APT Weaver Ant infiltrated a telco in Asia. The popular xrpl.js Ripple cryptocurrency library was compromised, and British retailer Marks & Spencer managed a cyber incident. Multiple companies, including DaVita and Yale New Haven Health, disclosed data breaches. New malware variants, such as Ballista Botnet and Astral Foods, were discovered, and Cloak ransomware group hacked the Virginia Attorney General's Office. U.S. CISA added Ivanti Connect Secure and Policy Secure flaws to its catalog, and a member of the Scattered Spider cybercrime group pleaded guilty. China-linked group UNC5221 exploited Ivanti Connect Secure zero-day, and Europol-led operation shut down a CSAM platform. New Triada Trojan came preinstalled on Android devices, and FIN7's Anubis backdoor allowed full system control on Windows. U.S. CISA added Apache Tomcat flaw to its catalog, and Apple backported fixes for three actively exploited flaws. A spike in Palo Alto Networks scanner activity suggested imminent cyber threats, and Microsoft warned of a critical flaw in Canon printer drivers. France's antitrust authority fined Apple €150M for issues related to its App Tracking Transparency. Malicious NPM packages targeted PayPal users, and Tycoon2FA phishing kits were updated. Russia-linked Gamaredon targeted Ukraine with Remcos RAT, and CoffeeLoader used a GPU-based packer to evade detection. Morphing Meerkat phishing kits exploited DNS MX records, and U.S. CISA added Cisco Smart Licensing Utility flaw to its catalog. Denmark warned of increased state-sponsored campaigns targeting European telcos. A ransomware attack hit the Micronesian state of Yap, and LockBit ransomware developers were extradited. Medusa ransomware targeted critical infrastructure organizations, and China-linked APT UNC3886 targeted EoL Juniper routers. U.S. CISA added Microsoft Windows flaws to its catalog, and Microsoft fixed six actively exploited zero-days. A cyberattack hit Ukraine's national railway operator, and Chinese APT Weaver Ant infiltrated a telco in Asia. The popular xrpl.js Ripple cryptocurrency library was compromised, and British retailer Marks & Spencer managed a cyber incident. Multiple companies, including DaVita and Yale New Haven Health, disclosed data breaches. New malware variants, such as Ballista Botnet and Astral Foods, were discovered, and Cloak ransomware group hacked the Virginia Attorney General's Office. U.S. CISA added Ivanti Connect Secure and Policy Secure flaws to its catalog, and a member of the Scattered Spider cybercrime group pleaded guilty. China-linked group UNC5221 exploited Ivanti Connect Secure zero-day, and Europol-led operation shut down a CSAM platform. New Triada Trojan came preinstalled on Android devices, and FIN7's Anubis backdoor allowed full system control on Windows. U.S. CISA added Apache Tomcat flaw to its catalog, and Apple backported fixes for three actively exploited flaws. A spike in Palo Alto Networks scanner activity suggested imminent cyber threats, and Microsoft warned of a critical flaw in Canon printer drivers. France's antitrust authority fined Apple €150M for issues related to its App Tracking Transparency. Malicious N
April 25, 2025
In the intricate world of quantum physics, where particles interact in ways that seem to defy the standard rules of space and time, lies a profound mystery that continues to captivate scientists: the…

April 25, 2025 • By Yvonne Lau
Canadian tech needs more public and private investment from a diverse range of sources. Domestic firms rely heavily on U.S. investors to scale, and the country faces a critical shortage of growth-st…

April 25, 2025 • By TelecomTV Staff
Here's a concise summary of the news article: Intel's new CEO, Lip-Bu Tan, has announced a major restructuring of the company, including an unspecified headcount reduction and a revision of its AI strategy. The goal is to simplify operations, cut costs, and improve execution. Tan aims to reduce Intel's 2025 operating cost target by $500m to $17bn and then cut it by a further $1bn in 2026 to $16bn. In other news, T-Mobile US had a strong start to the year, with service revenues increasing by 5.2% year on year to $16.93bn. The company also announced that its 5G Advanced network is now nationwide, enabling creators to unlock next-generation experiences. AT&T has partnered with Helium Network to enable subscribers to access wireless connectivity in remote areas via Helium's decentralized "people-powered" platform. This move is part of AT&T's strategy to rely less on traditional networks and more on partnerships to broaden its reach. NEC has successfully conducted Japan's longest-ever terrestrial wireless free-space optical (FSO) communication over a distance of more than 10km. The company plans to make the technology commercially available by 2028 and combine it with quantum cryptography to develop free-space quantum key distribution technology. A US House select committee has subpoenaed China's three major telcos, alleging that they continue to maintain "points of presence" in the US and exploit them to help enable cyberattacks. The committee is investigating the companies' connections to the Chinese military and government. Finally, Patrick Drahi is looking to sell his stake in Altice France, having secured a debt-for-equity deal with bondholders in February. The telecom billionaire is keen on a sale to a single buyer, but speculation suggests that France's other three main telcos may join forces and share the spoils.

April 25, 2025 • By Matthew Sparkes
Researchers warn that hackers may be able to tamper with results on shared quantum computers, potentially giving users incorrect results. This vulnerability will worsen as quantum devices grow and host more users. However, manufacturers can address this security gap to prevent issues. Currently, classical supercomputers have security measures to prevent user interference, but similar protections are needed for quantum computers.

April 25, 2025 • By Janesh Janardhanan, Forbes Councils Member, Janesh Janardhanan, Forbes Councils Member https://www.forbes.com/councils/forbesbusinessdevelopmentcouncil/people/janeshjanardhanan/
The article "Are You Ready For The Coming Transformation?" by Janesh Janardhanan discusses the importance of businesses being prepared for transformation in order to survive and thrive. The author notes that companies like Nokia, Kodak, and BlackBerry failed to adapt to changing circumstances and ultimately failed. Janardhanan identifies eight strategic imperatives that businesses should focus on to prepare for transformation: 1. Innovative business models 2. Compression of value chains 3. Transformative mega trends 4. Disruptive technologies 5. Internal challenges 6. Competitive intensity 7. Geopolitical chaos 8. Industry convergence The author emphasizes that real transformation requires a cultural shift and a mindset change across the entire organization, involving cross-functional collaboration, strategic prioritization, and the discipline to accept and learn from failure. By building a transformation-ready culture, businesses can gain a competitive advantage and be better equipped to pivot with agility in response to changing circumstances. The article concludes that transformation is inevitable, and companies that make future readiness an organizational habit will be the ones that survive and thrive.
April 25, 2025 • By Pierluigi Paganini
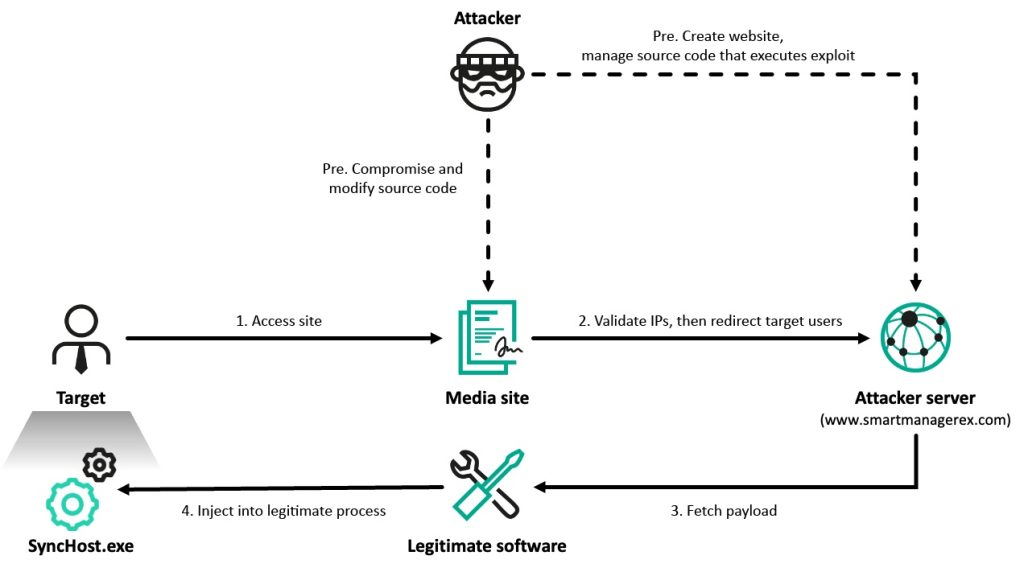
Here is a concise summary of the news article in 8173 tokens or less: Multiple cybersecurity incidents have been reported, including data breaches at MTN Group, DaVita, and Yale New Haven Health, affecting millions of patients. Ransomware attacks have targeted various organizations, such as Interlock, which leaked data from a kidney dialysis firm, and LockBit, which exploited Fortinet Firewall flaws. Several vulnerabilities have been discovered, including a zero-day in Ivanti Connect Secure, a flaw in Apache Parquet's Java Library, and a critical flaw in Cisco Smart Licensing Utility. Nation-state actors, such as China-linked APT groups, have been involved in various cyberattacks, including the exploitation of vulnerabilities in Juniper routers and the use of custom malware. Other notable incidents include a cyberattack on the Micronesian state of Yap, a data breach at the US Treasury's OCC, and a warning from the US CISA about increased cyber threats against the energy sector. Cybersecurity firms have also reported on various malware campaigns, including the use of Android spyware, crypto mining campaigns, and phishing kits. Overall, the cybersecurity landscape remains complex and ever-evolving, with various threats and vulnerabilities emerging daily.

April 25, 2025 • By Rohit Garg, Ankit Awasthi
The article discusses the potential of distributed cloud computing combined with Privacy Enhanced Technologies (PETs) and Artificial Intelligence (AI) to create a secure and private data processing framework. Distributed cloud computing allows data to be processed in a decentralized manner, reducing reliance on centralized servers and minimizing the risk of data breaches. PETs, such as homomorphic encryption and secure multi-party computation, enable secure data analysis without compromising individual privacy. AI can be integrated into this landscape to enable intelligent decision-making, automation, and enhanced security. The article highlights the benefits of PETs, including secure data collaboration, compliance, and security, and explores practical applications, such as healthcare and finance. It also discusses future developments, including integrating edge computing, quantum computing, and decentralized data marketplaces. Overall, the article emphasizes the importance of trust in cloud computing and the potential of distributed cloud computing, PETs, and AI to create a robust and secure data processing framework.

April 25, 2025 • By Rohit Garg, Ankit Awasthi
The article discusses the potential of distributed cloud computing combined with Privacy Enhanced Technologies (PETs) and Artificial Intelligence (AI) to create a robust and secure data processing framework. Distributed cloud computing allows data to be processed in a decentralized manner, reducing reliance on centralized servers and minimizing the risk of data breaches. PETs, such as homomorphic encryption and secure multi-party computation, enable secure data analysis without compromising individual privacy. AI can be integrated into this landscape to enable intelligent decision-making, automation, and enhanced security. The article highlights the benefits of PETs, including secure data collaboration, compliance, and improved data security. It also explores practical applications, such as healthcare and finance, where distributed cloud computing and PETs can be used to analyze sensitive data while maintaining privacy. The future of cloud computing is expected to involve integrating edge computing, quantum computing, autonomous data management, and decentralized data marketplaces, with a focus on trust and human-centered design principles.
April 25, 2025 • By Pierluigi Paganini
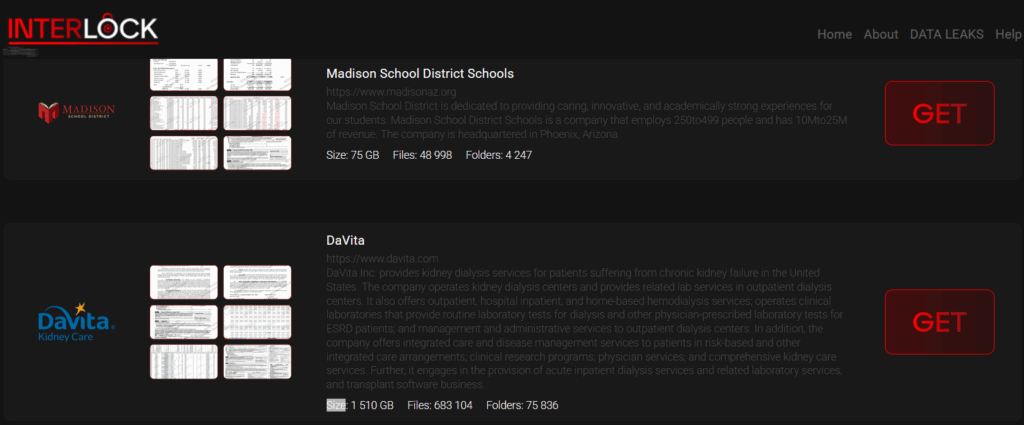
Here is a concise summary of the news article in 8173 tokens or less: Multiple cybersecurity incidents have been reported, including data breaches at MTN Group, DaVita, and Yale New Haven Health, affecting millions of patients. Ransomware attacks have targeted various organizations, such as Interlock, which leaked data from a kidney dialysis firm, and LockBit, which exploited Fortinet Firewall flaws. Several malware campaigns have been discovered, including DslogdRAT, SuperCard X, and ResolverRAT, which target healthcare and pharmaceutical firms. Nation-state actors, like China-linked APT groups, have been involved in cyberattacks, including the exploitation of Ivanti Connect Secure zero-day flaws. The US Cybersecurity and Infrastructure Security Agency (CISA) has added several vulnerabilities to its Known Exploited Vulnerabilities catalog, including Apple products, Microsoft Windows, and Cisco Smart Licensing Utility flaws. Google has fixed several actively exploited flaws, including a Chrome zero-day, and WhatsApp has introduced Advanced Chat Privacy to protect sensitive communications. Other notable incidents include the compromise of the xrpl.js Ripple cryptocurrency library, a supply chain attack on British retailer Marks & Spencer, and a cyberattack on Ukraine's national railway operator. The FBI has warned of malicious free online document converters spreading malware, and a cybercrime group has been arrested for stealing $8.2 million in a romance baiting crypto fraud scheme.